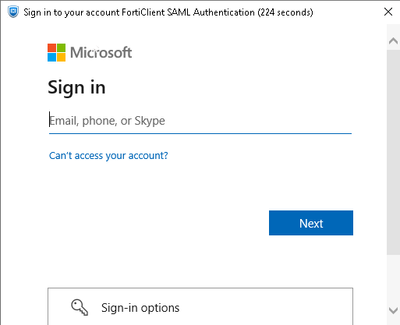
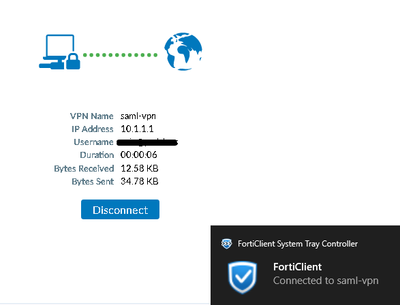
This article describes how to configure Dial-up IPsec VPN with Microsoft Entra ID SAML authentication.
Scope
FortiGate v7.2.0 or later and FortiClient v7.2.4 or later.
Solution
FortClient v7.2.4 or later is supports SAML with Dial-up IPsec VPN only with IKEv2.
The below steps show how to create a Dial-up IPsec VPN with Microsoft Entra ID (formerly known as Azure AD) SAML.
- Configure the auth-ike-saml-port under in the FortiGate as shown below:
config sys global
set auth-ike-saml-port 9443
end
- Configure the VPN certificate under user setting:
config user setting
set auth-cert “Fortinet_Factory”
end
- Configure SAML on the FortiGate and use the custom ike-saml-port in the address field:
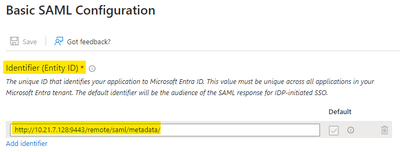
- Create an Enterprise application in Microsoft Entra ID. Follow the below guide to create this enterprise application: Technical Tip: Configuring SAML SSO login for FortiGate administrators with Entra ID acting as SAML …
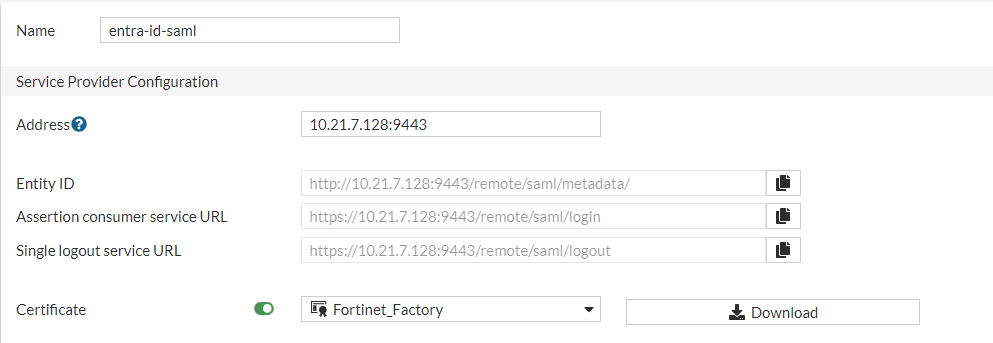
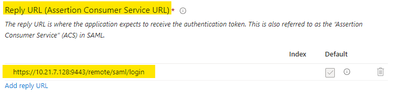
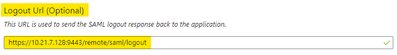
- The Service provider configuration from Step 3 should be populated in the SAML Application in Azure as shown in the below screenshots:
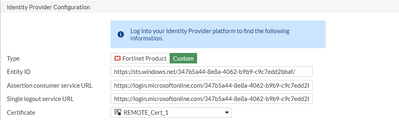
- Identity provider configuration from Azure should be populated in the SAML configuration on the FortiGate as shown below:
- SAML configuration on the FortiGate should look like this:
config user saml
edit “entra-id-saml”
set cert “Fortinet_Factory”
set entity-id http://10.21.7.128:9443/remote/saml/metadata/
set single-sign-on-url https://10.21.7.128:9443/remote/saml/login
set single-logout-url https://10.21.7.128:9443/remote/saml/logout
set idp-entity-id https://sts.windows.net/347b5a44-8e8a-4062-b9b9-c9c7edd2bbaf/
set idp-single-sign-on-url https://login.microsoftonline.com/347b5a44-8e8a-4062-b9b9-c9c7edd2bbaf/saml2
set idp-single-logout-url https://login.microsoftonline.com/347b5a44-8e8a-4062-b9b9-c9c7edd2bbaf/saml2
set idp-cert “REMOTE_Cert_1″
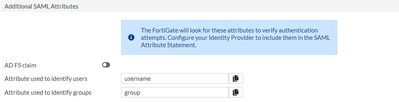
set user-name “username”
set group-name “group”
set digest-method sha1
next
end
- Configure ike-saml-server under the listening interface:
config system interface
edit “port2″
set ike-saml-server “entra-id-saml”
next
end
- Configure user group with the SAML server:
config user group
edit “ike-saml”
set member “entra-id-saml”
next
end
- Configure Dial-up IPsec VPN:
config vpn ipsec phase1-interface
edit “saml-vpn”
set type dynamic
set interface “port2″
set ike-version 2
set peertype any
set net-device disable
set mode-cfg enable
set proposal des-sha1 des-sha256 aes128gcm-prfsha256 aes256gcm-prfsha384 chacha20poly1305-prfsha256
set dpd on-idle
set eap enable
set eap-identity send-request
set authusrgrp “ike-saml”
set ipv4-start-ip 10.1.1.1
set ipv4-end-ip 10.1.1.254
set dns-mode auto
set psksecret ENC CmD7ySUqMXY6GCRYGsxQr7FQ8HY2H40+g0Ywimpcxlqgi4m7sYX4ws5d+eMM0YziovFdilnwJP/k5bM/Tdcomj4d2u/umne03oq71aekERi4xOUcJk+yh1KKgmgoA2ek9EX8L6egnByAFqynQIIzufV0bwKz+1DiXl+T3A3MiZ+cA7ePRL5WeAgUXP4wfEx+4FEoKQ==
set dpd-retryinterval 60
next
end
Note that EAP might cause issue while connecting. The debug will be showing gw validation failed.
Simply disable EAP in phase 1.
config vpn ipsec phase2-interface
edit “saml-vpn”
set phase1name “saml-vpn”
set proposal aes128-sha1 aes256-sha1 aes128-sha256 aes256-sha256 aes128gcm aes256gcm chacha20poly1305
next
end
- Configure firewall policy:
config firewall policy
edit 0
set name “saml-vpn”
set srcintf “saml-vpn”
set dstintf “port2″
set action accept
set srcaddr “all”
set dstaddr “all”
set schedule “always”
set service “ALL”
set nat enable
next
end
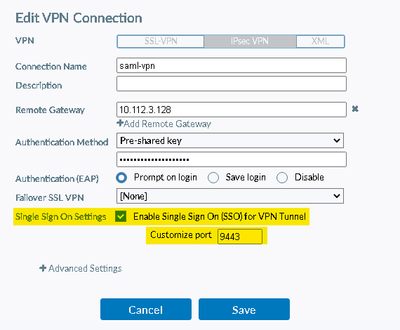
On the user machine, Configure IPsec VPN with SSO for VPN tunnel enabled and customize the port as set in step 1:
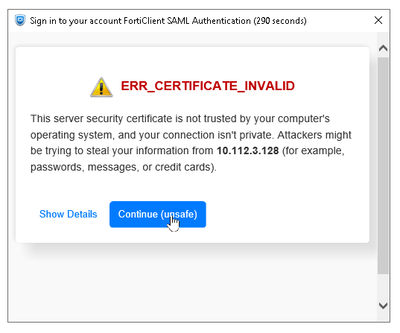
If an untrusted certificate is used in Step 2, FortiClient will show this warning:
Users can now log in using Entra ID SAML to the Dial-up IPsec VPN.
Troubleshooting:
Execute the following commands to enable debugging on the FortiGate, then reproduce the issue if there is one:
diag debug console timestamp enable
diag debug app fnbamd -1
diag debug app saml -1
diag debug app ike -1
diag debug enable
Note:
Dial-up IPsec with SAML does not support using an external browser for authentication. This feature is expected to be added in v7.6.1+.
5,292 total views, 16 views today