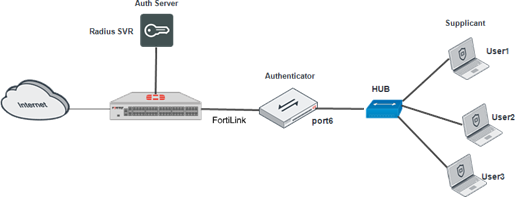
This article describes how to configure MAC-based 802.1X authentication to managed FortiSwitch ports when using FortiLink.
Managed FortiSwitch will authenticate and record the MAC addresses of user units.
If there is a hub after the FortiSwitch that connects multiple user units, each unit can access the network after passing authentication.
- The certificates and authentication protocol supported by the supplicant software and RADIUS server are compatible.
- The managed FortiSwitches using FortiLink act as authenticators.
# config firewall policy
edit <policy_ID>
set srcintf “fortilink-interface”
set dstintf “outbound-interface-to-RadiusSVR”
set srcaddr “all”
set dstaddr “all”
set action accept
set schedule “always”
set service “RADIUS”
set nat enable
next
end
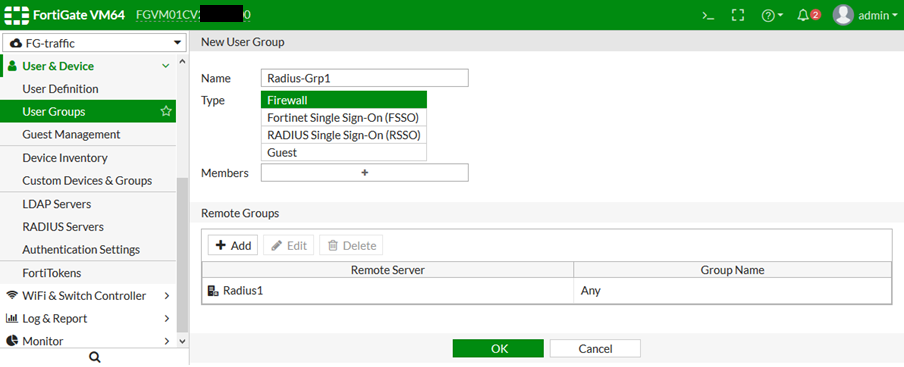
2) Designate a RADIUS server and create a user group.
# config user radius
edit “Radius1″
set server “172.18.60.203″
set secret ENC 1dddddd
next
end
# config user group
edit “Radius-Grp1″
set member “Radius1″
next
end
From GUI.
- On the FortiGate, go to User & Device -> RADIUS Servers.
- Edit an existing server, or create a new one.
- If necessary, add a Name for the server.
- Set the IP/Name to 172.18.60.203 and Secret to 1dddddd .
- Configure other fields as necessary.
- Select ‘OK’.
- Go to User & Device -> User Groups.
- Create a new group, and add the RADIUS server to the Remote Groups list.
- Select ‘OK’.
# config switch-controller security-policy 802-1X
edit “802-1X-policy-default”
set security-mode 802.1X-mac-based
set user-group “Radius-Grp1″
set mac-auth-bypass disable
set open-auth disable
set eap-passthru enable
set guest-vlan disable
set auth-fail-vlan disable
set framevid-apply enable
set radius-timeout-overwrite disable
next
end
Configure the guest VLAN, authentication fail VLAN, and other parameters as needed.
From GUI.
- Go to Wi-Fi & Switch Controller -> FortiSwitch Security Policies.
- Use the default 802-1X-policy-default, or create a new security policy.
- Use the RADIUS server group in the policy.
- Set the Security mode to MAC-based.
- Configure other fields as necessary.
- Select ‘OK’.
4) Apply the security policy to the ports of the managed FortiSwitches.
# config switch-controller managed-switch
edit S248EPTF1800XXXX
# config ports
edit “port6″
set port-security-policy “802-1X-policy-default”
next
end
next
end
On the FortiSwitch, check the configuration.
# config switch interface
edit “port6″
set allowed-vlans 4093
set untagged-vlans 4093
set security-groups “Radius-Grp1″
set snmp-index 6
# config port-security
set auth-fail-vlan disable
set eap-passthru enable
set framevid-apply enable
set guest-auth-delay 30
set guest-vlan disable
set mac-auth-bypass disable
set open-auth disable
set port-security-mode 802.1X-mac-based
set radius-timeout-overwrite disable
set auth-fail-vlanid 200
set guest-vlanid 100
end
next
end
From GUI.
- On the FortiGate, go to WiFi & Switch Controller -> FortiSwitch VLANs.
- Configure the VLAN interfaces that are applied on FortiSwitch.
- On FortiGate, these switch VLAN interfaces are treated as layer-3 interfaces and are available to be applied by firewall policy and other security controls in FortiOS. This means that security boundary is extended to FortiSwitch.
Results.
Execute 802.1X authentication on a user unit.
On Linux, run wpa_supplicant.
wpa_supplicant -c /etc/wpa_supplicant/local_supplicant.conf -D wired -i eth2 -dd
On the FortiGate, view the status of the 802.1X authentication:
diagnose switch-controller switch-info 802.1X
Managed Switch : S248EPTF1800XXXX
port6 : Mode: mac-based (mac-by-pass disable) <—– MAC-based.
Link: Link up
Port State: authorized: ( ) <—– Showing authorized means auth passed. Otherwise, shown failed.
EAP pass-through mode : Enable
Native Vlan : 1
Allowed Vlan list: 1,4093
Untagged Vlan list: 1,4093
Guest VLAN :
Auth-Fail Vlan :
Switch sessions 1/240, Local port sessions:1/20
Client MAC Type Vlan Dynamic-Vlan
00:0c:29:d4:4f:3c 802.1x 1 0 <—– User unit of auth passed can access the network. Its MAC address is recored, while other User units under same FSW ports still not allowed to access.
Sessions info:
00:0c:29:d4:4f:3c Type=802.1x,MD5,state=AUTHENTICATED,etime=6,eap_cnt=3 params:reAuth=3600
3,632 total views, 2 views today